I hope you have read the Part-I of this post and successfully blocked the ads. Now this part of the article is for those who want to dig deep in the system of ad injection.
As I mentioned earlier that this whole system works on transparent proxy.
What is Transparent Proxy?
Also known as an intercepting proxy or forced proxy, a transparent proxy intercepts normal communication at the network layer without requiring any special client configuration. Clients need not be aware of the existence of the proxy. A transparent proxy is normally located between the client and the Internet, with the proxy performing some of the functions of a gateway or router.”A ‘transparent proxy’ is a proxy that does not modify the request or response beyond what is required for proxy authentication and identification”.
“A ‘non-transparent proxy’ is a proxy that modifies the request or response in order to provide some added service to the user agent, such as group annotation services, media type transformation, protocol reduction, or anonymity filtering”.
(from wikipedia.org)
How to detect a Transparent Proxy?
1. For this you need a Linux Box. Here I’ll show you using Ubuntu 12.04.
- Login to your Linux Box either directly or using SSH
- Type : tcptraceroute flipkart.com 80
- Press Enter
- Again Type : tcptraceroute flipkart.com 443
- Press Enter
No what we do here is, first we perform a traceroute to the flipkart.com website on port 80 (http) which is generally intercepted by Proxy Servers. We find the following route information.
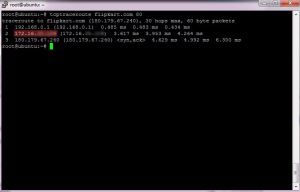
Then We again do a tcptraceroute on the port 443 (https) of flipkart.com. Voila ! The route is completely different which indicates that there is a proxy server which intercepts the http traffic.
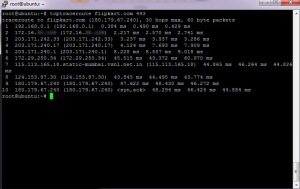
The IP Address masked is the gateway provided by my ISP. So after comparing these two results, we can conclude that there is a transparent proxy server which sits between the ISP and the webserver (here flipkart.com).
2. There is another way to detect an operating squid server and this method can be used in widwows too. Here we check whether the HTTP (TRACE) request headers are modified between the client and server.
- Go the the run dialog box by pressing the Windows button + R
- write cmd, press ok.
- Then type : telnet cmyip.com 80
- Then paste :
GET / HTTP/1.0
Host: www.cmyip.com

- Press enter twice
- You will get the following output.
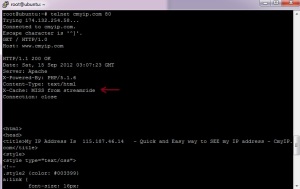
As we can see that X-Cache: MISS from streamride, which means the content is served via the streamride server powered by squid which is also used to inject ads.
I think you got some idea on how they intercept HTTP Traffic.

