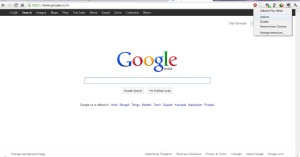
For couple of month I and several other cable broadband users in Kolkata have been the victim of advertisement codes injected by various Internet Service Providers (ISPs) for their revenue. This has degraded the browsing experience of users. So after several research and google’ing about these ads I found some interesting results which I’m going to share with you all here.
This all started with the “streamride.net” ad which the users noticed in the source code of all the webpages they browsed. This resulted in an ad window in the bottom of the webpage which covered up the contents of the main webpage. This page appeared in all non-ssl (http) websites but was not seen in secured (https) websites & done by using “Transparent Proxy” which will discussed in details in Part-II. First of I would like to tell you that this “streamride” is a product from a business named “Envisage Media” based in Delhi. According to their website they describe their product as
Streamride is a software platform, which provides valuable technology services to internet service providers, helping them be commercially viable. Its innovative and unique structure makes it highly reliable, easy to deploy and maintain.
The following code is used to inject the ad into the webpage.
<div id="sTREAMrIDE" class="9;14"></div>
<script type="text/javascript" src="http://ui.streamride.net/ui.js"></script>
Recently some ISP like Alliance Broadband modified the code keeping their function same-Serving Ads
<div id="S1D3P4G3" class="7;48"></div> <script type="text/javascript" src="http://ui.sidepage.co/3/ui.prod.old.js"></script>
The above codes are placed at the starting of the <body> tag in every webpages. This ‘ui.js’ is the source for the ads which initiates ad scripts from zedo.com and other ad publishers.
Method-1 (If you have single PC)
Many people suggest adding a host entry in the ‘host’ file in windows or linux. The process is already discussed in several blogs, wont go through it again here. Check out http://bit.ly/JYNvuG for a “How-To”.
Method-2 (Most Effective to be used with a Router)
Solution for users having Routers and for those who access internet through WiFi Devices. I’ll be showing here how to set up access blocking in a D-Link DIR-615 Router. The steps are:
1. Log into to your Router using your router’s IP Address.
2. Go to “Advanced” tab
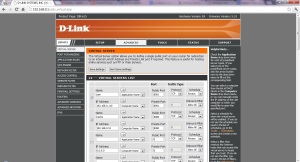
3. Click “Website Filter”
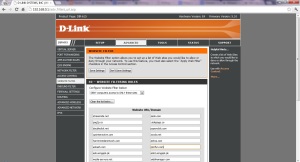
4. Ad these domain one by one
- streamride.net
- zedo.com
- pag2p.co
- sidepage.co
5. If you want you can put optional ad-serving domains as shown in the screenshot.
6. Click “Save Settings” then click “Continue”.
7. Now we need to set up Access Control, so we go to “Access Control” tab. Click “Add Policy”.
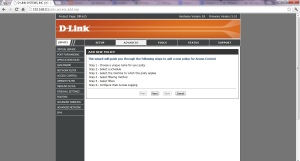
8. Give a name to your policy. Then Click Next.
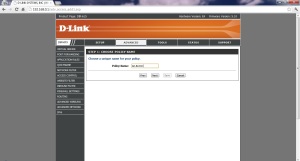
9. Again click Next. Now here we have to configure the IP Address of the devices we want the “Url/Domain Blocking” to be applied.
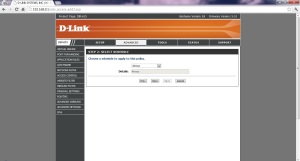
10. Give the IP or the MAC Address of the device(s). ( I would recommend you to assign a static DHCP Lease for your WiFi Device like Smartphones etc. for better administration.) Then Click Ok.
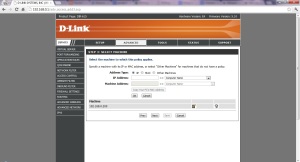
11. Click Next then select “Apply Web Filter”. Click Next, then click save.
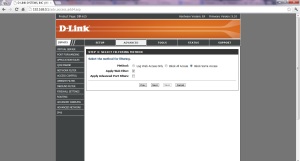
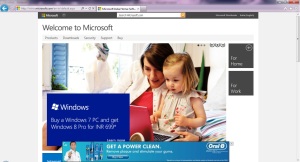
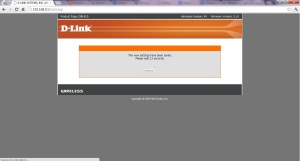
12. Your access control rule will be added in the list. Now try to access any of the sites that you blocked in Step-4, you will be shown the following page
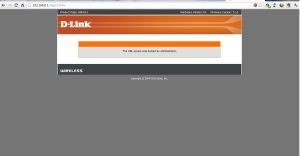
So what it basically did is simple – blocked access to those any of those domains and their subdomains. Thus you can get rid of those ads by setting this on your router and it will be applied in all the devices in your network by just putting in their IPs without the strenuous job of modifying the host file in every system.
Method – 3 (Simple yet useful for a couple of PCs)
In this method you have some minimum requirements like you must
- Use Chrome as your Default Browser
- Install these two most useful plugins from chrome store (https://chrome.google.com/webstore) – Adblock Plus (Beta) & Do Not Track Plus
Then we need to configure the AdBlock plus for blocking ads :
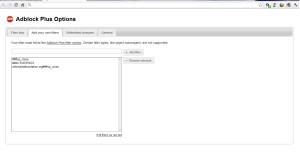
1. If you get ads from “streamride” then follow these steps:
- Right Click on the AdBlock plus logo on the Address Bar. Then Click “Options”.
- Click on “Add your own filters”.
- Write this : ##div.sTREAMrIDE
- Click Add Filter
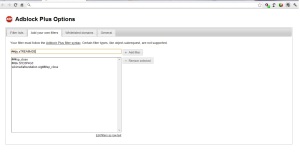
2. If you get ads from “sidepage” then follow these steps:
- Right Click on the AdBlock plus logo on the Address Bar. Then Click “Options”.
- Click on “Add your own filters”.
- Write this : ##div.S1D3P4G3
- Click Add Filter
- Then write : ##div.sp_frame
- Click Add Filter
That’s it. By following any of the above mentioned method you can block the ads injected by your ISP. Keep Checking out this post’s Part-II which I’ll write in a couple of days on some research in detail about how these ads are injected.